The story behind the SolarWinds malware attack and the implications for Cybersecurity
Views, News & more

What happened?
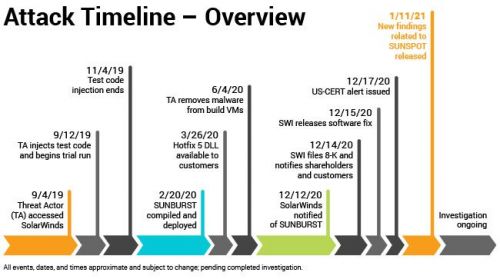
In December 2020, cybersecurity firm FireEye detected a malware attack being conducted through the Orion system of security vendor SolarWinds. Acknowledging the attack, SolarWinds described it as a “highly sophisticated, manual supply chain attack on SolarWinds Orion Platform software builds for versions 2019.4 HF 5 through 2020.2.1, released between March 2020 and June 2020.”
Beginning in March 2020, attackers, believed to be from the Russian Foreign Intelligence Service (SVR) had been able to add malware (later labelled “SunBurst”) to Orion software updates. This enabled them to gain a foothold in the Orion network, allowing attackers to forge single sign-on tokens to impersonate existing users and add their own credentials.
(Source: SolarWinds)
Who was impacted?
The attack has proven particularly shocking due to its scale, the fact it went seemingly completely undetected for several months and the prominence of those potentially affected. Around 33,000 organisations are thought to use the Orion system to manage their IT resources, with the malware potentially being distributed to around 18,000 of those.
Orion users include the US Pentagon, US State Department, all five branches of the US military, the White House, the NSA, the Department of Justice, NASA, over 425 of the US Fortune 500 companies, all of the top 10 US telecoms companies and hundreds of universities and colleges across the world.
Due to the stealthy nature of the attack and the fact it went undetected for so long, some security experts believe that many victims will never know whether they were compromised. It has at least been confirmed, however, that hackers accessed dozens of email accounts and networks in the US Treasury Department, including the highest-ranking officials in the Departmental Offices of the Treasury. It has been claimed that only unclassified Treasury information was accessed.
The Killswitch
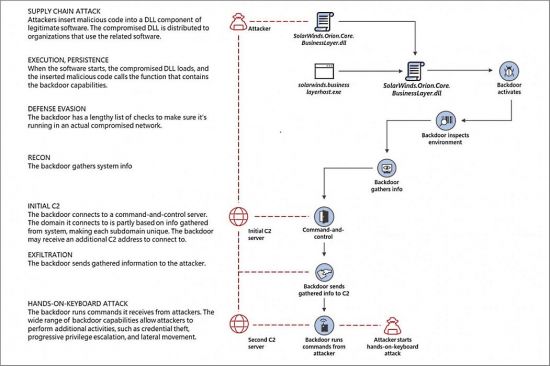
Shortly after the malware breach was disclosed, one of the malicious domains that hacked networks had been communicating with was seemingly taken into Microsoft’s control. The domain, avsvmcloud[.]com, was one of several set up by the attackers to control systems that they gained access to.
FireEye confirmed that the domain had been seized as part of a collaborative effort between itself, Microsoft and GoDaddy. FireEye added that the domain name had been reconfigured as a “killswitch” that could prevent Sunburst from continuing to operate.
In a statement, FireEye said: “Depending on the IP address returned when the malware resolves avsvmcloud[.]com, under certain conditions, the malware would terminate itself and prevent further execution. FireEye collaborated with GoDaddy and Microsoft to deactivate SUNBURST infections.”
“This killswitch will affect new and previous SUNBURST infections by disabling SUNBURST deployments that are still beaconing to avsvmcloud[.]com. However, in the intrusions FireEye has seen, this actor moved quickly to establish additional persistent mechanisms to access to victim networks beyond the SUNBURST backdoor.”
“This killswitch will not remove the actor from victim networks where they have established other backdoors. However, it will make it more difficult to for the actor to leverage the previously distributed versions of SUNBURST.”
(Source: Microsoft)
Is the danger passed?
Despite this positive development, the timescale and magnitude of the SolarWinds attack means it is impossible to know how successful a killswitch will be in tackling the damage done by the malware. Former Homeland Security Adviser Tom Brossert wrote that the “magnitude of this ongoing attack is hard to overstate.”
Brossert added: “The Russians have had access to a considerable number of important and sensitive networks for six to nine months. The Russian S.V.R. will surely have used its access to further exploit and gain administrative control over the networks it considered priority targets. For those targets, the hackers will have long ago moved past their entry point, covered their tracks and gained what experts call “persistent access,” meaning the ability to infiltrate and control networks in a way that is hard to detect or remove.
“While the Russians did not have the time to gain complete control over every network they hacked, they most certainly did gain it over hundreds of them. It will take years to know for certain which networks the Russians control and which ones they just occupy.”
What are the implications of the attack?
Given the widespread target surface of the attack, the first implication to consider is the time it will take to identify which systems, companies or organisations have been compromised, never mind the time and money then required to secure them.
As Tom Brossert writes: “The logical conclusion is that we must act as if the Russian government has control of all the networks it has penetrated. But it is unclear what the Russians intend to do next. The access the Russians now enjoy could be used for far more than simply spying.”
Thoughts then must turn to what the attackers may do with the access they have, which has implications not just for the US government and other companies and organisations affected, but for public trust in cybersecurity. If whatever access they have is used to spread misinformation, fake news, destroy or leak data or exert malign political influence, then public and consumer trust in cybersecurity could quickly erode.
Some have suggested that the profile of the attack could herald a new age in cybersecurity thinking, one in which organisations are not just preparing for, predicting or reacting to attacks, but assuming that they have already happened. This could have implications for how companies safeguard their systems and data, which will become far more complex to manage if the working assumption is that they are already under attack.
Finally, the stunning efficiency and success of the attack has led to widespread predictions that other attackers may increasingly employ similar techniques. FireEye director Matthew McWhirt said: "Now there are other actors that will obviously adopt these techniques, because they go after what works.”
Regarding the likelihood of increased supply chain attacks in future, Shaked Reiner of CyberArk says: “Even though it’s a difficult technique to perform, it still gives attacker a lot of crucial advantages that they need. Because the SolarWinds attackers used it so successfully I'm sure that other attackers will note this and use it more and more from now on.”
How can organisations protect themselves?
An attack of such magnitude is sure to come as a wakeup call to many, even those who already take cybersecurity seriously, and to result in a wide-scale rethinking of cybersecurity protocols. The National Security Agency (NSA), emphasised the importance of authentication when running products and systems.
The NSA wrote: “It is critical when running products that perform authentication that the server and all the services that depend on it are properly configured for secure operation and integration. Otherwise, SAML tokens could be forged, granting access to numerous resources.”
The attack has also reasserted the importance of minimising the amount of accounts that have privileges to use, interact with and modify authentication systems, while it will also be vital for network managers to have clear visibility of identity provider services, such as token signing certificates. Monitoring these kinds of tokens will be crucial, in order to spot and combat unusual activity early before real damage can be done.
Get in touch
020 7847 4510
We may process your personal information in order to send you information you request, measure and improve our marketing campaigns, and further our legitimate interests. For further details, see our privacy policy.
Contact us
-
- Head Office:
- hSo, 50 Leman Street, London, E1 8HQ
- Switchboard:
- 020 7847 4500
- Support (24x7):
- 0333 200 3337
- support@hso.co.uk
- Marketing & Sales:
- 020 7847 4510
- info@hso.co.uk

















